What Is the ARP Command and How Does It Work?
TL;DR
- ARP command maps IP addresses to MAC addresses, enabling effective device communication within local networks.
- ARP works between OSI layers 3 and 2, resolving addresses and caching data to enhance network efficiency.
- Network admins use ARP commands to view, add, delete ARP entries, clear cache, and troubleshoot on Windows, Linux, and macOS.
- Common uses include troubleshooting, detecting IP conflicts, discovering devices, auditing security, and ensuring accurate IP-MAC mappings.
- Unlike ping or traceroute, ARP excels at local network troubleshooting, Layer 2 issues, and security forensics.
- ARP spoofing threats are countered by static entries, dynamic inspection, network segmentation, and monitoring; mastering ARP speeds troubleshooting.
Network troubleshooting can feel like solving a puzzle with missing pieces. You know something’s wrong, but pinpointing the exact issue requires the right tools and knowledge.
The ARP command is one of those essential networking utilities that every IT professional should master. Whether you’re diagnosing connectivity issues, monitoring network devices, or securing your infrastructure, understanding how to use the ARP command effectively can save you hours of frustration.
After a decade of working in network administration, I’ve seen countless scenarios where the ARP command was the key to resolving complex network problems. From identifying rogue devices to troubleshooting IP conflicts, this simple yet powerful tool has proven invaluable time and again.
This comprehensive guide will walk you through everything you need to know about the ARP command. You’ll learn how it works, master the essential commands across different operating systems, and discover practical applications that will make you more effective in your network management role.
By the end of this post, you’ll have the confidence to use ARP commands for troubleshooting, security auditing, and network optimization.
What Does ARP Stand For in Networking?
ARP stands for Address Resolution Protocol. This fundamental networking protocol serves as a bridge between the network layer (Layer 3) and data link layer (Layer 2) in the OSI model.
Think of ARP as a translator that helps devices communicate on local networks. When your computer wants to send data to another device on the same network, it needs to know both the IP address (logical address) and the MAC address (physical address) of the destination device.
Role of Address Resolution Protocol
The Address Resolution Protocol maintains a mapping table that associates IP addresses with their corresponding MAC addresses. This table, known as the ARP table or ARP cache, stores recent mappings to improve network efficiency.
Here’s what happens when ARP is working:
- Your device checks its ARP table for the destination MAC address
- If the mapping exists, data transmission proceeds immediately
- If the mapping is missing, an ARP request broadcasts across the network
- The target device responds with its MAC address
- Your device updates its ARP table with the new mapping
Why ARP is Critical for IP-MAC Communication
Without ARP, devices on the same network segment couldn’t communicate effectively. IP packets need MAC addresses to traverse Ethernet networks, making ARP an essential component of modern networking.
The protocol operates transparently in the background, handling thousands of address resolution requests without user intervention. However, understanding ARP becomes crucial when network issues arise or security concerns emerge.
How Does the ARP Command Work?
The ARP command provides direct access to your system’s ARP table, allowing you to view, modify, and troubleshoot address mappings. Understanding the underlying process helps you use these commands more effectively.
Step-by-Step Explanation of IP-to-MAC Mapping
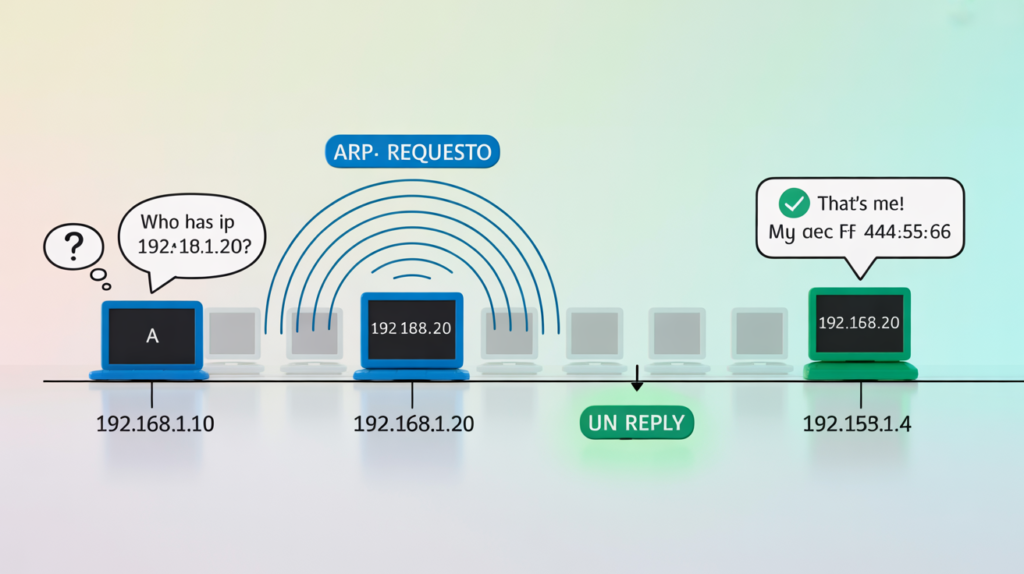
When a device needs to communicate with another device on the local network, the ARP process follows these steps:
Step 1: ARP Table Lookup
The sending device first checks its local ARP table for the destination IP address. If a valid entry exists, the communication proceeds immediately.
Step 2: ARP Request Generation
If no entry exists, the device creates an ARP request packet containing:
- Sender’s IP address
- Sender’s MAC address
- Target IP address
- Empty target MAC address field
Step 3: Broadcast Transmission
The ARP request broadcasts to all devices on the local network segment using the broadcast MAC address (FF:FF:FF:FF:FF:FF).
Step 4: Target Response
Only the device with the matching IP address responds with an ARP reply containing its MAC address.
Step 5: Cache Update
Both devices update their ARP tables with the new mapping information for future communications.
Understanding ARP Requests and Replies
ARP requests and replies use specific packet formats that network administrators can analyze with protocol analyzers or packet capture tools.
ARP requests are broadcast messages, meaning every device on the network segment receives them. This broadcast nature makes ARP both functional and potentially vulnerable to security attacks.
ARP replies are unicast messages sent directly back to the requesting device. The bidirectional nature ensures both devices maintain updated mapping information.
Common ARP Commands in Windows, Linux, and macOS
Mastering ARP commands across different operating systems makes you more versatile as a network professional. Each platform offers similar functionality with slight syntax variations.
arp -a Command Usage and Output
The arp -a command displays the complete ARP table on your system. This is probably the most frequently used ARP command in daily network administration.
Windows Output Example:
Interface: 192.168.1.100 --- 0x8
Internet Address Physical Address Type
192.168.1.1 00-50-56-c0-00-01 dynamic
192.168.1.10 00-1b-44-11-3a-b7 dynamic
192.168.1.255 ff-ff-ff-ff-ff-ff static
Linux Output Example:
Address HWtype HWaddress Flags Mask Iface
192.168.1.1 ether 00:50:56:c0:00:01 C eth0
192.168.1.10 ether 00:1b:44:11:3a:b7 C eth0
The output reveals valuable information including IP addresses, MAC addresses, entry types (dynamic or static), and network interfaces.
Viewing and Managing ARP Tables Across Operating Systems
Different operating systems provide various options for viewing and filtering ARP table information.
Windows Commands:
arp -a– Display all ARP entriesarp -a -N 192.168.1.100– Show entries for specific interfacearp -g– Alternative syntax for displaying entries
Linux Commands:
arp -a– Display ARP table in BSD formatarp -e– Display ARP table in default formatip neigh show– Modern alternative using ip command
macOS Commands:
arp -a– Display all ARP entriesarp -n– Display entries without hostname resolutionnetstat -rn– Show routing table with ARP information
Adding and Deleting ARP Entries Manually
Static ARP entries can be useful for troubleshooting or security purposes. Manual ARP management requires administrative privileges on most systems.
Adding Static Entries:
Windows: arp -s 192.168.1.10 00-1B-44-11-3A-B7
Linux: arp -s 192.168.1.10 00:1b:44:11:3a:b7
macOS: arp -s 192.168.1.10 00:1b:44:11:3a:b7
Deleting Specific Entries:
Windows: arp -d 192.168.1.10
Linux: arp -d 192.168.1.10
macOS: arp -d 192.168.1.10
Static entries persist until manually removed or system restart, making them valuable for testing scenarios or security implementations.
How to Clear or Flush the ARP Cache
Clearing the ARP cache resolves many network connectivity issues caused by stale or incorrect address mappings. Different operating systems use distinct commands for cache management.
Windows: netsh interface ip delete arpcache
Windows provides multiple methods for clearing the ARP cache:
Method 1 – NetSh Command:
netsh interface ip delete arpcache
Method 2 – ARP Command:
arp -d *
The netsh command provides more comprehensive cache clearing, while the arp command offers granular control over specific entries.
Linux: ip neigh flush all
Linux systems offer several approaches to ARP cache management:
Modern Method:
ip neigh flush all
Traditional Method:
arp -d -a
Interface-Specific Clearing:
ip neigh flush dev eth0
The ip command provides more advanced functionality and is the preferred method for modern Linux distributions.
When to Clear ARP Cache (Troubleshooting Reasons)
Several scenarios require ARP cache clearing for effective troubleshooting:
Network Configuration Changes
When devices receive new IP addresses or MAC addresses change, stale ARP entries can cause connectivity failures.
Security Incidents
ARP spoofing attacks may corrupt cache entries, requiring immediate clearing and investigation.
Hardware Replacements
Replacing network interface cards or entire devices necessitates ARP cache updates to prevent communication issues.
Intermittent Connectivity
Clearing ARP cache often resolves mysterious connectivity problems that resist other troubleshooting attempts.
Regular cache clearing during troubleshooting eliminates variables and provides a clean starting point for diagnosis.
What Are the Most Common Use Cases of ARP Command?
Understanding practical applications helps you leverage ARP commands effectively in real-world scenarios. These use cases represent situations you’ll encounter regularly in network administration.
Network Troubleshooting
ARP commands excel at diagnosing Layer 2 connectivity issues that other tools might miss.
Connectivity Verification
Check if devices can resolve each other’s addresses by examining ARP table entries after ping attempts.
Gateway Problems
Verify default gateway MAC address resolution when experiencing internet connectivity issues.
Switch Port Issues
Identify port-specific problems by monitoring ARP entries for devices connected to specific switch ports.
VLAN Configuration
Troubleshoot VLAN misconfigurations by examining which devices appear in ARP tables across different network segments.
Detecting Duplicate IPs
IP address conflicts create significant network disruption. ARP commands help identify and resolve these conflicts quickly.
Conflict Identification
Multiple devices claiming the same IP address will generate conflicting ARP entries with different MAC addresses.
Change Monitoring
Watching ARP table changes over time reveals devices that might be receiving dynamic IP addresses already in use.
Static Assignment Verification
Confirm static IP assignments don’t conflict with DHCP allocations by monitoring ARP entries.
Monitoring Devices in Local Networks
ARP tables provide real-time visibility into active devices on your network segments.
Device Discovery
Populate ARP tables by pinging broadcast addresses, then examine results to discover active devices.
Security Auditing
Regular ARP table reviews help identify unauthorized devices that might have connected to your network.
Asset Management
Track device locations and movements by monitoring MAC addresses across different network segments.
ARP Command vs Ping vs Traceroute — When to Use Each?
Choosing the right diagnostic tool depends on the specific network problem you’re investigating. Each tool provides unique insights into different aspects of network connectivity.
Comparing Tools for Network Diagnostics
ARP Command Strengths:
- Layer 2 address resolution troubleshooting
- Local network device discovery
- MAC address verification
- Security investigation of address conflicts
Ping Command Strengths:
- End-to-end connectivity testing
- Round-trip time measurement
- Packet loss detection
- Basic reachability verification
Traceroute Command Strengths:
- Path discovery between networks
- Router hop identification
- Latency analysis per hop
- Routing problem diagnosis
Best Scenarios to Apply ARP Over Other Tools
Use ARP commands when you need to:
Investigate Local Network Issues
ARP provides detailed information about devices on the same network segment that ping cannot reveal.
Verify Hardware Address Resolution
When IP connectivity works but performance suffers, ARP commands help identify MAC address resolution problems.
Security Forensics
ARP tables contain evidence of device activity that other tools might miss during security investigations.
Troubleshoot Switching Problems
Layer 2 issues require ARP-level diagnosis since ping operates at Layer 3 and might miss switching-related problems.
ARP Security Concerns: What Is ARP Spoofing?
ARP’s trust-based design creates security vulnerabilities that attackers can exploit. Understanding these threats helps you implement appropriate protective measures.
How Attackers Exploit ARP Tables
ARP spoofing attacks manipulate the address resolution process to redirect network traffic through attacker-controlled systems.
Attack Methodology:
- Attacker sends unsolicited ARP replies to target devices
- Victims update their ARP tables with attacker’s MAC address
- Network traffic intended for legitimate devices routes to attacker
- Attacker can intercept, modify, or block communications
Common Attack Scenarios:
- Man-in-the-middle attacks between clients and gateways
- Session hijacking on wireless networks
- Denial of service through ARP flooding
- Network reconnaissance and device enumeration
Mitigation Strategies for ARP Spoofing Attacks
Implementing multiple defense layers provides comprehensive protection against ARP-based attacks.
Static ARP Entries
Configure critical device mappings as static ARP entries to prevent spoofing attacks.
Dynamic ARP Inspection
Enable switch-based Dynamic ARP Inspection (DAI) to validate ARP packets against DHCP snooping bindings.
Network Segmentation
Limit ARP broadcast domains through VLANs and network segmentation to reduce attack surface.
Monitoring Solutions
Deploy network monitoring tools that alert on suspicious ARP activity or rapid table changes.
Port Security
Configure switch port security features to prevent unauthorized devices from connecting to network segments.
Advanced ARP Techniques for Network Engineers
Experienced network professionals can leverage ARP commands in sophisticated ways to automate tasks and integrate with larger network management systems.
Using ARP in Scripts and Automation
ARP commands integrate well with scripting languages for automated network management tasks.
PowerShell Example – Windows:
$arpTable = arp -a | Select-String "192.168.1"
foreach ($entry in $arpTable) {
# Process each ARP entry for analysis
}
Bash Example – Linux:
#!/bin/bash
for ip in $(arp -a | grep "192.168.1" | cut -d'(' -f2 | cut -d')' -f1); do
echo "Processing device: $ip"
done
Automation enables regular ARP table auditing, device discovery, and security monitoring without manual intervention.
Integrating ARP Checks in Network Monitoring Tools
Modern network monitoring platforms can incorporate ARP data for comprehensive visibility.
SNMP Integration
Query device ARP tables via SNMP to centralize address resolution monitoring.
API Development
Create custom APIs that expose ARP information for integration with ticketing systems or dashboards.
Database Storage
Store historical ARP data in databases for trend analysis and forensic investigation.
Alert Generation
Configure alerts for specific ARP events like new device detection or address conflicts.
ARP Command Not Working? Troubleshooting Tips
When ARP commands fail to execute or produce unexpected results, systematic troubleshooting helps identify and resolve the underlying issues.
Checking Admin Privileges
Most ARP table modifications require elevated privileges across all operating systems.
Windows Solutions:
- Run Command Prompt as Administrator
- Use PowerShell with elevated privileges
- Check User Account Control (UAC) settings
Linux Solutions:
- Use sudo prefix for ARP commands
- Switch to root user for extensive troubleshooting
- Verify user group memberships for network access
macOS Solutions:
- Use sudo for administrative ARP operations
- Check System Integrity Protection (SIP) status
- Verify Terminal application permissions
Verifying Interface Configuration
Network interface problems can prevent ARP commands from functioning correctly.
Interface Status Checks:
- Verify network adapters are enabled and functional
- Check IP address assignments and subnet configurations
- Confirm interface MTU settings don’t block ARP packets
Driver Issues:
- Update network adapter drivers to latest versions
- Check for hardware compatibility problems
- Verify interface binding configurations
Firewall or Driver-Related Issues
Security software and driver problems frequently interfere with ARP operations.
Firewall Configuration:
- Temporarily disable host-based firewalls for testing
- Check ARP packet filtering rules
- Verify network profile settings allow local traffic
Driver Troubleshooting:
- Reinstall network adapter drivers
- Check for driver conflicts in device manager
- Test with different network adapters if available
Software Conflicts:
- Identify VPN software that might interfere
- Check virtualization software network settings
- Verify third-party security software configurations
Why Every Network Professional Should Master ARP
The ARP command remains one of the most valuable tools in a network administrator’s toolkit. Its simplicity belies its power in diagnosing complex network issues and maintaining network security.
Real-World Applications
Throughout my career, I’ve relied on ARP commands in countless situations:
- Resolving mysterious connectivity issues that stumped other diagnostic tools
- Identifying security breaches through unusual ARP table entries
- Optimizing network performance by understanding device communication patterns
- Training junior administrators on fundamental networking concepts
The versatility and reliability of ARP commands make them essential knowledge for anyone serious about network administration.
Quick Reference Recap
Keep these essential ARP commands readily available:
arp -a– Display ARP tablearp -d [IP]– Delete specific entryarp -s [IP] [MAC]– Add static entrynetsh interface ip delete arpcache– Clear cache (Windows)ip neigh flush all– Clear cache (Linux)
Mastering these commands provides the foundation for advanced network troubleshooting and security analysis.
The investment in learning ARP commands pays dividends throughout your networking career. From troubleshooting basic connectivity issues to investigating security incidents, ARP commands provide insights that other tools simply cannot match.
📘 Bonus Section – ARP Command Examples
Here are practical ARP command examples you can use immediately:
Basic Commands
# Show ARP Table
arp -a
# Show ARP entries for specific interface (Windows)
arp -a -N 192.168.1.100
# Show ARP table in Linux default format
arp -e
Management Commands
# Add Static ARP Entry
arp -s 192.168.1.10 00-1B-44-11-3A-B7
# Delete specific ARP Entry
arp -d 192.168.1.10
# Delete all ARP entries (Windows)
arp -d *
Advanced Operations
# Clear ARP cache (Windows)
netsh interface ip delete arpcache
# Clear ARP cache (Linux)
ip neigh flush all
# Show only incomplete entries (Linux)
arp -a | grep incomplete
These examples provide starting points for your own ARP command usage. Practice with these commands in test environments before applying them to production networks.
FAQs
What does ARP stand for, and why is it important?
How does the ARP command work on a network?
What is the step-by-step ARP process for IP-to-MAC mapping?
How can you view and manage ARP tables on different operating systems?
When should you clear or flush the ARP cache, and how is it done?
What are some common use cases for ARP commands in networks?
ARP commands are essential for network troubleshooting, detecting duplicate IPs, auditing devices on local networks, and resolving Layer 2 connectivity issues. They help identify conflicts and unauthorized devices, contributing to more secure and efficient networks.
How can ARP commands help protect against network security threats?
ARP spoofing is a common attack where false mappings are inserted into ARP tables. Mitigation strategies include using static ARP entries, enabling Dynamic ARP Inspection, monitoring suspicious ARP activity, and applying switch port security to strengthen network protection.