
HTTP Status Code 401 Unauthorized Explained – How to Fix and Prevent It
TL;DR
- HTTP 401 errors occur when the server can’t verify your identity due to missing or incorrect authentication credentials. Access to protected resources is denied until valid credentials are provided.
- Common causes include wrong passwords, expired or missing tokens, malformed authorization headers, or server misconfigurations after updates or migrations.
- The 401 Unauthorized error means the server requests authentication, unlike 403 Forbidden which denies permission even if authentication is valid.
- Users can fix 401 errors by re-entering credentials carefully, clearing browser cookies and cache, resetting passwords, or contacting support if needed.
- Website owners should verify authentication settings (.htaccess, nginx), update or reset API keys/tokens, ensure SSL certificates are valid, and check server logs for errors.
- Prevent 401 errors with strong authentication methods like multi-factor authentication, proper session management, regular updates to authentication systems, and monitoring logs for suspicious activity.
Expanded Overview of HTTP 401 Troubleshooting and Authentication Challenges
When dealing with web authentication errors, HTTP 401 troubleshooting often starts with a review of how the server validates user credentials. Understanding the broader landscape of HTTP error codes, particularly the distinction between authentication vs authorization, is key for users and developers alike. Websites and APIs rely on authorization headers and secure user session management to ensure that only legitimate users have access to protected resources.
You’re trying to access a website or API, and suddenly you’re hit with a “401 Unauthorized” error. Frustrating, right?
Don’t worry. I’ve been dealing with web authentication issues for over a decade. I’ve seen this error pop up countless times across different projects.
The good news? HTTP Status code 401 errors are usually fixable. Whether you’re a website owner, developer, or just a regular user, this guide will help you understand what’s happening and how to resolve it.
Let’s dive in and get your access back on track.
What Is HTTP Status Code 401?
Definition of 401 Unauthorized Error
HTTP status code 401 means “Unauthorized.” It’s your server’s way of saying, “I don’t know who you are, so I can’t let you in.”
Think of it like a bouncer at an exclusive club. You need to show proper ID (authentication) to get past the door.
When you see a 401 error, it means the server received your request but couldn’t verify your identity. The resource you’re trying to access requires authentication, and something went wrong with that process.
The HTTP 401 response is frequently seen when access control fails, for example if the correct authorization header is not sent or is rejected by the server. This can also be caused by problems in API authentication backing web services or membership site login forms. Secure login practices, such as using multi-factor authentication and strong passwords, can help minimize the risk of unauthorized access and 401 errors.
Difference Between 401 and 403 Forbidden
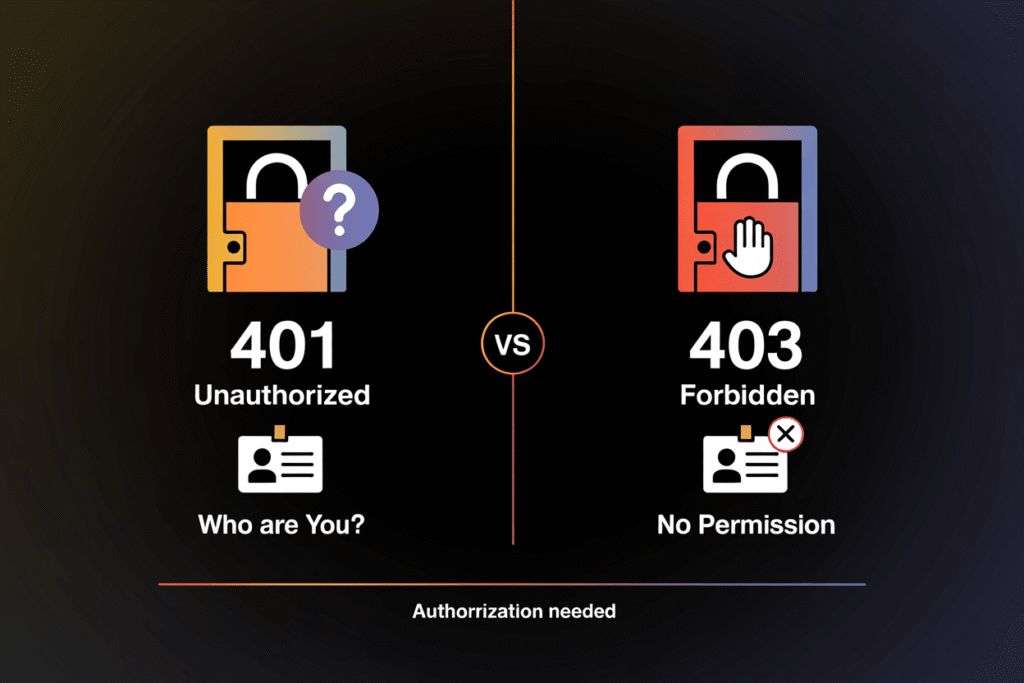
Here’s where many people get confused. Both 401 and 403 errors block your access, but for different reasons.
A 401 error means the server doesn’t know who you are. You haven’t provided valid credentials yet.
A 403 error means the server knows exactly who you are, but you don’t have permission to access that resource. It’s like having a valid ID but not being on the VIP list.
In simple terms: 401 = “Who are you?” and 403 = “I know who you are, but you can’t come in.”
When troubleshooting HTTP status responses, remember that 401 errors point to authentication problems, while 403 errors deal with authorization. Incorporating website security best practices, such as error message customization, can provide users with meaningful information without exposing sensitive details.
Why Does HTTP Status Code 401 Occur?
Invalid or Missing Authentication Credentials
The most common cause is wrong or missing login information. Maybe you typed your password incorrectly. Or your username has changed.
I’ve seen this happen when users copy-paste credentials and accidentally include extra spaces. Those invisible characters can break authentication.
Sometimes the credentials are completely missing from the request. This happens when authentication tokens get stripped out during the request process.
Misconfigured authentication can result from missing or malformed authorization headers, errors with JWT token validation, or API authentication changes. Carefully reviewing the authentication method and any hosting support for authentication setup is essential in HTTP 401 troubleshooting.
Expired or Invalid Session Tokens
Modern web applications use session tokens or API keys for authentication. These tokens have expiration dates.
When a token expires, the server can’t verify your identity anymore. You’ll get a 401 error until you refresh the token or log in again.
I’ve noticed this happens a lot with mobile apps. Users leave an app open for days, and when they return, their session has expired.
A common API authentication problem is the JWT token error, where either the token has expired or its signature no longer matches. Such errors can also be triggered by poor user session management, including improper session timeout settings.
Misconfigured Authentication Settings in the Server
Server configuration issues can trigger false 401 errors. The authentication system might be pointing to the wrong database. Or the server settings don’t match the expected authentication method.
This is especially common after server migrations or updates. Settings that worked perfectly before suddenly start rejecting valid credentials.
Server misconfiguration, especially regarding SSL authentication problems, can result in valid credentials being rejected. In REST API security, strict configuration is needed, including correct SSL/TLS settings and accurate authentication headers.
How to Identify a 401 Unauthorized Error?
Browser Error Messages
Different browsers show 401 errors in different ways. You might see messages like:
- “401 Authorization Required”
- “Access Denied”
- “Authentication Required”
- “Unauthorized”
Some websites customize these messages. But they all mean the same thing: authentication failed.
Error message customization not only assists users but helps developers differentiate between HTTP error codes when providing support.
Server Response Headers and Logs
If you’re technically minded, check the HTTP response headers. A 401 response includes a “WWW-Authenticate” header that tells you what authentication method the server expects.
Server logs are goldmines for diagnosing 401 errors. They’ll show exactly when the authentication failed and why.
Ongoing server log analysis is crucial for HTTP 401 troubleshooting. Reviewing logs allows for timely detection of session timeouts, repeated failed logins from bots, and possible brute-force attempts, supporting overall website security best practices.
Using Debugging Tools to Trace Requests
Developer tools in your browser can help you trace the authentication process. Look at the Network tab to see if authentication headers are being sent correctly.
Tools like Postman are great for testing API authentication. You can see exactly what’s happening with each request.
Carefully review the HTTP WWW-Authenticate header to determine what type of credentials the server is requesting. For APIs and RESTful services, this header is often required for client code or third-party integrations to properly automate secure login practices.
How to Fix HTTP Status Code 401 as a User?
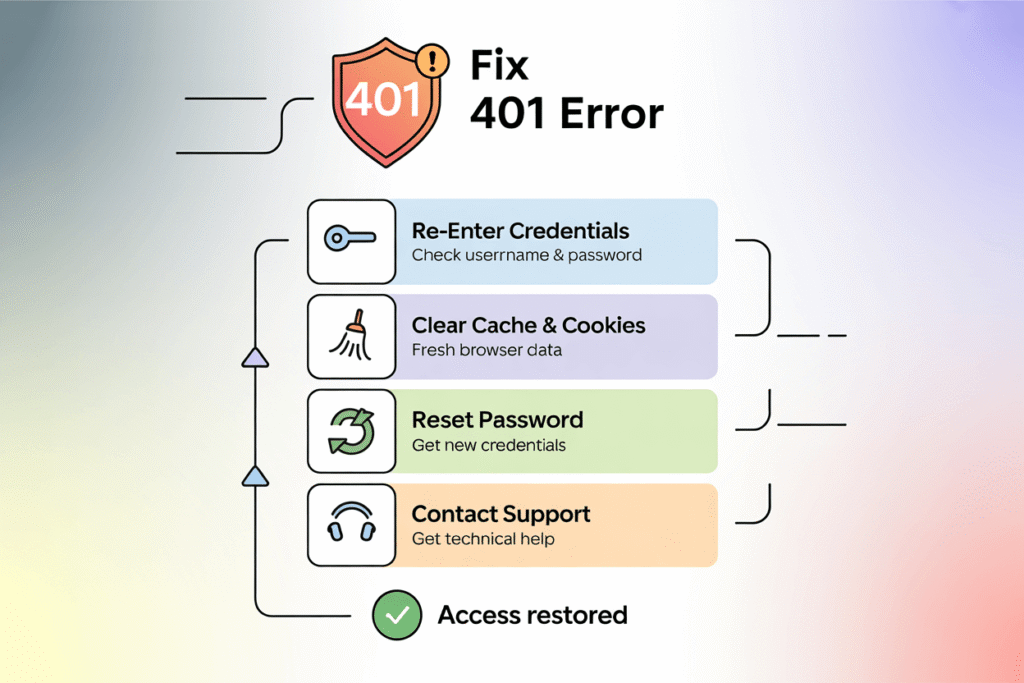
Re-entering Login Credentials Correctly
Start with the basics. Double-check your username and password. Make sure Caps Lock isn’t on.
Try typing your credentials manually instead of using auto-fill. Sometimes saved passwords get corrupted or outdated.
If you’re still having trouble, try resetting your password. Many 401 errors disappear after a fresh password reset.
A sound password reset process is a fundamental part of any membership site login system or API-driven application. Reliable user session management and clear error messages assist both admins and users in recovering from authentication interruptions.
Clearing Browser Cookies and Cache
Old authentication cookies can cause problems. They might contain expired session data that confuses the server.
Clear your browser’s cookies and cache for the specific website. Then try logging in again with fresh credentials.
I recommend clearing data for just the problematic site rather than your entire browser. This saves you from losing data on other websites.
Browser cookie clearing can resolve issues where session timeouts or lingering authentication data interfere with the login process, aligning with recommendations for website security best practices.
Checking Authentication with the Website or API
Contact the website support team if the above steps don’t work. There might be an issue on their end.
For API access, verify your API key is still valid. Check if there are any changes to the authentication requirements.
Sometimes services update their authentication methods. What worked last month might not work today.
Collaborating with hosting support for authentication problems ensures that misconfigurations, SSL authentication problems, or necessary API key changes are handled promptly.
How to Fix HTTP Status Code 401 as a Website Owner?
Verify Authentication Configurations in .htaccess or Nginx
Check your server configuration files. Look for authentication rules in .htaccess (Apache) or nginx.conf (Nginx).
Make sure the authentication method matches what your application expects. If you’re using basic authentication, verify the user database path is correct.
I’ve seen cases where relative paths break after server changes. Always use absolute paths for authentication files.
Authentication setup must also consider robots.txt vs authentication, as robots.txt does not provide real protection—HTTP authentication is required. Server misconfiguration can result in public or private resources being incorrectly protected.
Update or Reset API Keys and Tokens
Rotate your API keys regularly. Old or compromised keys should be revoked immediately.
If you’re using JWT tokens, check the signing key. A mismatch here will cause all authentication attempts to fail.
Generate new tokens and update your applications to use them. Don’t forget to update any documentation or client applications.
This practice is a core component of REST API security and broader HTTP 401 troubleshooting.
Ensure SSL/TLS Certificates Are Properly Configured
Authentication often requires HTTPS. If your SSL certificate is expired or misconfigured, authentication might fail.
Check your certificate status and renewal dates. Modern browsers are strict about SSL errors and may block authentication on insecure connections.
SSL authentication problems can block even valid login attempts, so it’s critical to maintain proper certificate management.
Contact Hosting Provider for Assistance
If you’re stuck, reach out to your hosting provider. Companies like Skynethosting.net offer 24/7 support to help with server configuration issues.
Hosting providers can check server logs and configurations that you might not have access to. They can often spot issues that aren’t obvious from the application side.
Access to hosting support for authentication troubleshooting shortens downtime and brings expert eyes to recurring or complex 401 error cases.
How Does HTTP Status Code 401 Affect SEO and Website Performance?
Impact on Crawlability and Indexing
Search engines can’t index pages that return 401 errors. This makes sense – these pages require authentication that search bots don’t have.
However, if public pages accidentally return 401 errors, you’ll lose search rankings. Google can’t index what it can’t access.
Monitor your search console for unexpected 401 errors on public content.
Issues with 401 error SEO impact go beyond loss of search traffic—they can severely hinder page crawlability, especially if error-prone resources are linked from elsewhere on your site.
Preventing Search Engines from Accessing Restricted Pages
Use 401 errors strategically to protect private content from search engines. This is better than relying on robots.txt alone.
Private user dashboards and admin panels should return 401 errors to unauthorized visitors, including search bots.
Comparing robots.txt vs authentication: robots.txt merely requests that bots don’t crawl certain pages, while HTTP authentication actively blocks all unauthorized access, humans and bots alike.
SEO Best Practices for Protected Content
Don’t use 401 errors on pages that should be publicly accessible. This will hurt your SEO performance.
For members-only content, consider showing a preview with a login prompt instead of a hard 401 error. This gives search engines something to index while still protecting your content.
Error message customization for SEO can include providing a “teaser” message while encouraging login, maximizing both user engagement and search engine crawlability.
How Can You Prevent HTTP Status Code 401 Errors?
Implement Secure Authentication Practices
Use strong authentication methods. Multi-factor authentication adds security without causing 401 errors for legitimate users.
Implement proper session management. Sessions should timeout appropriately – not too quickly to annoy users, but not so long that they become security risks.
Following website security best practices—such as enforcing secure login practices, applying access control, and monitoring for token tampering or session hijacking—will help reduce the frequency of HTTP status code 401 and related web authentication errors.
Regularly Update User Authentication Systems
Keep your authentication libraries and frameworks updated. Security patches often fix issues that could cause unexpected 401 errors.
Monitor authentication logs for patterns. A sudden spike in 401 errors might indicate an attack or system problem.
Periodic server log analysis is vital. Quick detection of brute-force login attempts or API authentication failures ensures prompt defenses are put in place.
Monitor Server Logs for Unauthorized Access Attempts
Set up alerts for unusual 401 error patterns. This helps you spot problems before they affect legitimate users.
Regular log analysis can reveal authentication issues you didn’t know existed. It’s also useful for capacity planning and security monitoring.
Comprehensive server log analysis strengthens overall REST API security and reveals underlying issues such as session timeout problems, JWT token errors, or server misconfiguration.
What You Should Remember About 401 Unauthorized Errors
Key Takeaways for Users and Developers
Status code 401 errors are authentication problems, not permission problems. The server needs to verify who you are.
Most 401 errors are fixable with basic troubleshooting: checking credentials, clearing cache, or updating tokens.
For developers, proper error handling makes 401 errors less frustrating for users. Provide clear instructions on how to resolve authentication issues.
Tools for HTTP 401 troubleshooting should include monitoring the HTTP WWW-Authenticate header, session timeout settings, user session management protocols, and regular browser cookie clearing.
Staying Secure While Maintaining Accessibility
Balance security with user experience. Strong authentication is important, but don’t make it so complex that legitimate users get locked out.
Implement proper error messages that help users without revealing sensitive information to attackers.
Secure login practices, including robust password reset processes and efficient user session management, ensure only authorized users gain access while also allowing for straightforward recovery in the event of authentication failures.
Reliable Hosting Support from Skynethosting.net
Having reliable hosting support makes a huge difference when dealing with authentication issues. Skynethosting.net’s 24/7 support team can help diagnose server-side authentication problems quickly.
With 20 years of hosting experience and support across 25 worldwide locations, they understand how to resolve complex authentication issues that cause 401 errors.
Trustworthy hosting support for authentication is invaluable for resolving persistent SSL authentication problems, optimizing REST API security, and ensuring maximum website uptime.
Remember, authentication problems can happen to anyone. The key is understanding what’s causing the issue and knowing how to fix it systematically.
FAQs
What does HTTP Status Code 401 mean?
A 401 Unauthorized error means the server couldn’t verify your identity due to missing or invalid authentication credentials. Authentication failed, so access is denied until valid credentials are provided. It’s a signal to authenticate before trying again
How is 401 different from 403 Forbidden?
A 401 error means you haven’t proven your identity—authentication credentials are missing or invalid. In contrast, 403 Forbidden means the server knows who you are but you lack permission to access the resource, even with proper authentication.
What causes a 401 Unauthorized error?
Common causes include incorrect passwords, expired or missing authentication tokens, or server misconfiguration. It can also result from invalid or missing authorization headers, session timeouts, or issues after server or authentication method updates.
How can a user fix a 401 error?
Users should carefully re-enter credentials, clear browser cookies and cache for the specific site, or reset their password. If the error persists, contacting the website’s support team or checking API key validity may resolve authentication issues.
How do website owners resolve 401 errors?
How do expired session tokens trigger 401 errors?
Session or API tokens are often time-limited. Once they expire, the server cannot authenticate the user or application until a new token is obtained or the user logs in again, resulting in a 401 unauthorized response.
What should developers check in the event of a 401 error?
Developers should examine server logs, HTTP response headers (like WWW-Authenticate), and make sure authorization headers are formatted and sent correctly. Checking for misconfigured authentication methods or mismatched token signatures is also vital.
How do 401 errors impact SEO?
Pages that return 401 status codes cannot be crawled or indexed by search engines. If public-facing pages return 401 errors, it could harm search rankings. Site owners must ensure only private content is protected by 401 responses.
How can 401 Unauthorized errors be prevented?
Implement strong authentication methods, maintain updated authentication libraries, monitor server logs for failed login attempts, and set appropriate session timeouts. Regularly update and rotate API keys or tokens, and ensure configuration matches security best practices.
What role does hosting support play in resolving 401 errors?
Reliable hosting support can help by diagnosing server-side authentication problems, reviewing configurations, and assisting with SSL, API, or session issues. Their expertise can quickly resolve persistent or complex 401 errors, ensuring website uptime and security.
About the Author: Elias Vance is a Senior Infrastructure Engineer with over 15 years of experience in managing high-performance web servers and data center operations. He specializes in optimizing hosting environments for speed, security, and scalability. A passionate advocate for efficient web technology, Elias leverages his deep technical expertise to help businesses and developers build faster, more reliable online platforms, including robust virtualization environments.



